Data Sharing + Storing
General Guidelines
- Share/store only data that is necessary, and make sure access remains limited to those who need it
- Keep data/files only as long as needed
- Use care when saving files and remember where you’ve saved them
- Consider saving and opening in Google Drive instead of your hard drive!
- Use good data and file management hygiene (review and wipe unneeded files frequently)
- Notify the Help Desk if you’re concerned about data you’ve received or how you received it
Sharing Confidential/Sensitive Data
Here are the recommended approaches for sharing sensitive data, in order of preference:
1) Leave Data in the System of Record
Whenever possible, share information from within the system of record.
2) Google Drive/Shared Drive
Sharing controls in Google Drive + Shared Drives allow you to control who has access to files.
3) Link to Drive File via Gmail
Link to files via the Google Drive icon, instead of attaching them with the paperclip icon.
4) Consult with Tech Services
If you are unsure about how to proceed, contact the Technology Services Help Desk.
Read more about each of these methods below!

Share/Store within System of Record
CCA has official records/data stored in several systems, including Workday, Salesforce, Raiser's Edge, TouchNet, and Symplicity.
Whenever possible, sensitive data should remain stored and shared within its native system or record. Each of these systems supports sharing of information and affords tight controls over data access.
Tools/Features:
All systems have reporting tools, including custom reporting. Consult with Tech Services or the appropriate Data Steward if access is needed to one of these systems.
Data Controls within System of Record:
The following controls are available to protect documents shared within the system of record.
✅ System access requires CCA credentials and, if enabled, Duo authentication
✅ Access automatically lost when CCA account disabled
✅ Sharing or forwarding of data can be tightly controlled
✅ Enterprise management tools (i.e. Tech Services can monitor and protect files)
✅ Data access enabled/segmented based on security role assigned in system

Google Drive/Shared Drive
Shared drives in Google have less sophisticated security role functionality than systems of record, but they are particularly useful for data necessitating prolonged team access (even when team members change over time). Shared drives also enable seamless, real-time collaboration.
Tools/Features:
Sharing controls in Google Drive, as well as for Shared Drives, allow you to share files only with those who need access.
Share settings in Shared Drives:
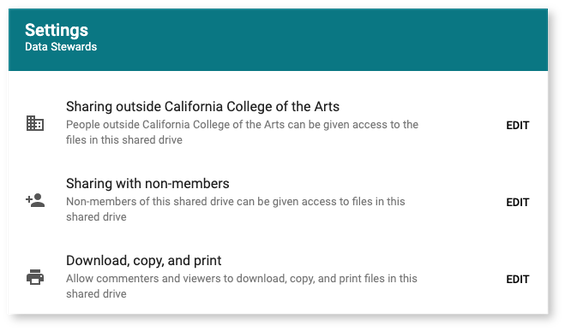
- Using shared drives, you can manage file access in relation to your organization as a whole or in relation to drive membership.
- By implementing desired share settings drive-wide, you can save time securing files individually, since they will inherit those share settings by default.
- You can also control whether viewers can copy, download, or print files, thereby preventing unauthorized versions of files included in the shared drive.
For additional information, read Google's shared drive documentation.
Share settings in Google Drive:
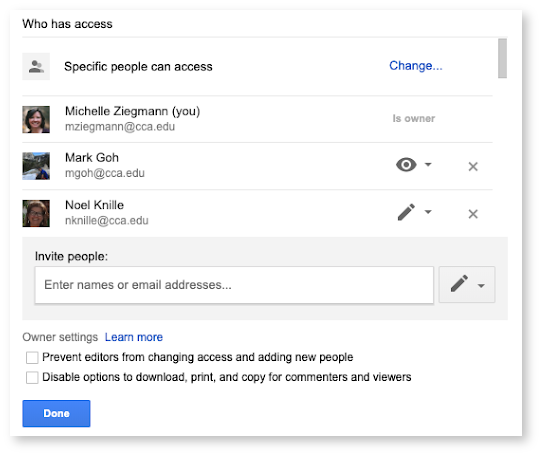
- You can also individually secure and/or share files in your personal Google Drive, but the controls are slightly different than with shared drives.
- You can designate different levels of access to specific individuals, some of whom may need to edit a shared file and some of whom may simply need to view it and/or comment on it.
- Additionally, as the owner of a file, you can prevent:
- those with editing access from changing share settings or adding new people
- viewers/commenters from downloading, printing, or copying the file
For more tips like this, check out Google's documentation on file sharing in Drive.
Data Controls within Google Drive/Shared Drives:
✅ System access requires CCA credentials and, if enabled, Duo authentication
✅ Access automatically lost when CCA account disabled
✅ Sharing or forwarding of data can be tightly controlled
✅ Enterprise management tools (i.e. Tech Services can monitor and protect files)
❌ Data access enabled/segmented IS NOT based on security role assigned in system

Gmail Link to Drive File (Not Attachment)
If you need to share confidential or sensitive files over email, you should do so by sharing/including Google Drive links rather than by attaching email files. Links help you retain control over access to the data and prevents copies from being made without your authorization.
Tools/Features:
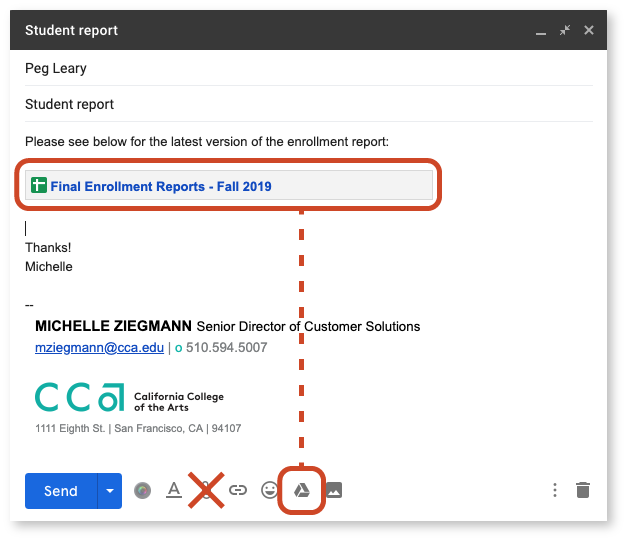
Avoid clicking the paperclip icon in the Gmail message footer, which will attach a downloadable copy of your file over which you have no further control.
Instead, when composing a message, click on the Google Drive icon to insert a link to the desired Google Drive or shared drive file (see image below).
This way, you still retain control of the data being shared and can limit further sharing or revoke access when necessary.
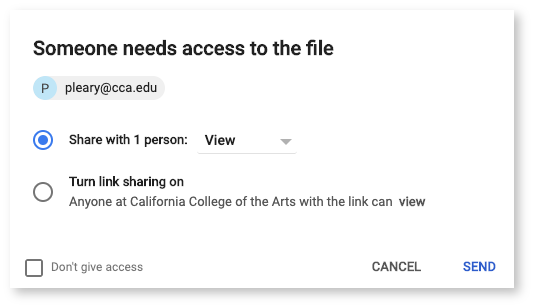
Gmail is even smart enough to let you know when you're sending someone a Google Drive file link that they don't have access to.
Google will prompt you grant the recipient access to view, comment, or edit the file. Alternatively, you can restrict access to the file in case one or more recipient really shouldn't have access to the linked file. This can sometimes be the case when sending a group email, which may include people outside of your team, project, or department.
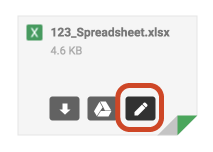
If you receive potentially sensitive or confidential data as an Excel or Word file attachment in an email, Google now lets you view/edit those docs directly in Google Drive, saving you the trouble of managing/deleting a downloaded file later.
Hover over the attached file, then click the pencil icon on the right. It should say Edit with Google Sheets for Excel files or Edit with Google Docs for Word files.
Best Practices with File Sharing in Gmail:
- Do not attach private data.
- Link to Google Drive instead.
- Share with care! Pay attention to sharing settings when prompted.
Data Controls Using Link to Drive:
✅ System access requires CCA credentials and, if enabled, Duo authentication
✅ Access automatically lost when CCA account disabled
✅ Sharing or forwarding of data can be tightly controlled
✅ Enterprise management tools (i.e. Tech Services can monitor and protect files)
❌ Data access enabled/segmented IS NOT based on security role assigned in system
Data Controls Using File Attachment:
❌ System access DOES NOT require CCA credentials and, if enabled, Duo authentication
❌ Access IS NOT automatically lost when CCA account disabled
❌ Sharing or forwarding of data CAN NOT be tightly controlled
❌ NO enterprise management tools (i.e. Tech Services has limited availability to monitor and protect files)
❌ Data access enabled/segmented IS NOT based on security role assigned in system

When in Doubt, Consult with Tech Services!
If you are unsure about how to proceed with storing and/or sharing potentially sensitive data, please submit an inquiry to the Help Desk. Please provide as much detail as possible about your requirements.
Technology Services is happy to provide guidance to ensure that information is shared safely and securely.